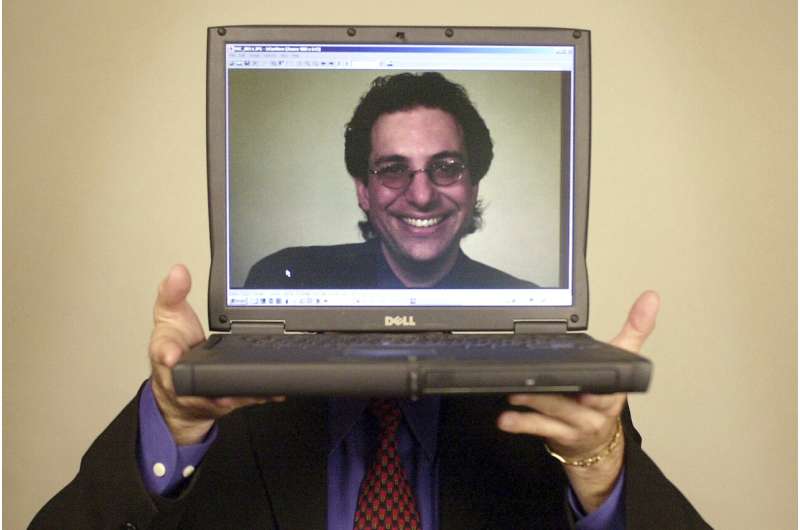
Kevin Mitnick, whose pioneering antics tricking employees in the 1980s and 1990s into helping him steal software and services from big phone and tech companies made him the most celebrated U.S. hacker, has died at age 59.
Mitnick died Sunday in Las Vegas after a 14-month battle with pancreatic cancer, said Stu Sjouwerman, CEO of the security training firm KnowBe4, where Mitnick was chief hacking officer.
His colorful career—from student tinkerer to FBI-hunted fugitive, imprisoned felon and finally respected cybersecurity professional, public speaker and author tapped for advice by U.S. lawmakers and global corporations—mirrors the evolution of society’s grasp of the nuances of computer hacking.
Through Mitnick’s professional trajectory, and what many consider the misplaced prosecutorial zeal that put him behind bars for nearly five years until 2000, the public has learned how to better distinguish serious computer crime from the mischievious troublemaking of youths hellbent on proving their hacking prowess.
“He never hacked for money,” said Sjouwerman, who became Mitnick’s business partner in 2011. He was mostly after trophies, chiefly cellphone code, he said.
Much fanfare accompanied Mitnick’s high-profile arrest in 1995, three years after he’d skipped probation on a previous computer break-in charge. The government accused him of causing millions of dollars in damages to companies including Motorola, Novell, Nokia and Sun Microsystems by stealing software and altering computer code.
But federal prosecutors had difficulty gathering evidence of major crimes, and after being jailed for nearly four years, Mitnick reached a plea agreement in 1999 that credited him for time served.
Upon his January 2000 release from prison, Mitnick told reporters his “were simple crimes of trespass.” He said “I wanted to know as much as I could find out about how phone networks worked.”
He was initially barred for three years from using computers, modems, cell phones or anything else that could give him internet access—and from public speaking. Those requirements were gradually eased but he wasn’t allowed back online until December 2002.
Mitnick’s forte was social engineering. He would impersonate company employees to obtain passwords and data, a technique known as pretexting that remains among the most effective in hacking and which typically requires considerable research to pull off successfully.
“His ingenuity challenged systems, incited dialogues, and pushed boundaries in cybersecurity. He will remain a testament to the uncharted power of curiousity,” tweeted Chris Wysopal, who as a member of the white-hat hacking group L0pht testified before the U.S. Senate a few years before Mitnick did the same.
“My hacking activity actually was a quest for knowledge, the intellectual challenge, the thrill and the escape from reality,” Mitnick said during a March 2000 congressional hearing in response to a question by Sen. Joseph Lieberman, D-Conn., about what motivated him.

In his prepared testimony, Mitnick boasted that he had “successfully penetrated some of the most resilient computer systems ever developed.”
Mitnick had first been arrested for computer crimes at age 17 for brazenly walking into a Pacific Bell office and taking a handful of computer manuals and codes to digital door locks. For that, he served a year in a rehabilitation center, deemed by a federal judge as being addicted to computer tampering.
Mitnick had been raised in the bleak Los Angeles suburb of Panorama City by his mother, who divorced his father when he was 3. An overweight, lonely teenager, he dropped out of high school and found friends only when he stumbled into the world of phone phreaks—teens who used stolen phone codes to make free long-distance calls.
Phones led to computers, and Mitnick showed himself to be a persistent, if not stellar, hacker. Enthralled by the possibility of using computers to gain access and power, Mitnick began breaking into voice mail and computer systems, rifling through private files and taunting those who crossed him.
But another side of Mitnick became clear in his conversations with investigative journalist Jonathan Littman printed in in the mid-1990s in “The Fugitive Game: Online with Kevin Mitnick.” The hacker seems less a threat than a fearful, disturbed young man, more annoying than vindictive.b
And though a computer file containing 20,000 credit card numbers copied from the internet service provider Netcom was found on Mitnick’s computer after a 1994 arrest, there is no evidence he ever used any of the accounts.
Mitnick became a cause celebre for hackers who considered his 5-year prison term excessive. Some defaced websites to post messages demanding his release. Among the targets was The New York Times—which some sympathizers accused of exaggerating the societal danger Mitnick posed.
Exaggerated stories of Mitnick’s exploits and abilities also made the rounds, sometimes fueling hysteria.
One led prison officials to put him in solitary confinment for nine months, said Sjouwerman, because they feared he could start a nuclear war by whistling into a pay phone—emulating a modem “to hack NORAD and trigger a ballistic missile.”
Mitnick is the author of “The Ghost in the Wires,” which recounts his adventures as a wanted hacker and three other books co-written with others including “The Art of Deception.”
In addition to his work at KnowBe4, where Mitnick was not involved in day-to-day operations, he ran a separate penetration-testing business with his wife, the former Kimberely Barry.
She is a native of Australia, where the two met.
© 2023 The Associated Press. All rights reserved. This material may not be published, broadcast, rewritten or redistributed without permission.
Citation:
Pioneering hacker Kevin Mitnick, FBI-wanted felon turned security guru, dead at 59 (2023, July 20)
retrieved 20 July 2023
from https://techxplore.com/news/2023-07-hacker-kevin-mitnick-fbi-wanted-felon.html
This document is subject to copyright. Apart from any fair dealing for the purpose of private study or research, no
part may be reproduced without the written permission. The content is provided for information purposes only.
Stay connected with us on social media platform for instant update click here to join our Twitter, & Facebook
We are now on Telegram. Click here to join our channel (@TechiUpdate) and stay updated with the latest Technology headlines.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
